Hello folks,
I have the following problem. I m trying to collect Windows events with Winlogbeat and send them to Graylog. Today I’ve noticed that Graylog duplicates the events with a different timestamp.
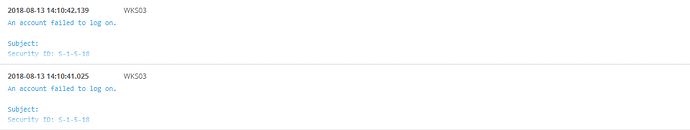
This is a test I’ve run to simulate an event with wrong credentials.
As you can see the times are different but the actual event is the same (when I check both events have the same account name. The one I’ve used for the test)
Here is the config of the Winlogbeat collector.
winlogbeat.event_logs:
- name: Microsoft-Windows-CAPI2/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 11
- equals.event_id: 70
- equals.event_id: 90
- name: Microsoft-Windows-DNS-Client/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 3008
- name: Microsoft-Windows-DriverFrameworks-UserMode/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 2004
- name: Microsoft-Windows-LSA/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 300
- name: Microsoft-Windows-PowerShell/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 4103
- equals.event_id: 4104
- equals.event_id: 4105
- equals.event_id: 4106
- name: Microsoft-Windows-SMBClient/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 30622
- equals.event_id: 30624
- name: Microsoft-Windows-TaskScheduler/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 106
- equals.event_id: 141
- equals.event_id: 142
- name: Microsoft-Windows-TerminalServices-RDPClient/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 1024
- name: Microsoft-Windows-Windows Defender/Operational
processors:
- drop_event.when.not.or:
- equals.event_id: 1006-1009
- equals.event_id: 1116-1119
- name: Application
processors:
- drop_event.when.not.or:
- equals.event_id: 1000
- equals.event_id: 1002
- equals.event_id: 1511
- equals.event_id: 1518
- name: Security
processors:
- drop_event.when.not.or:
- equals.event_id: 1100
- equals.event_id: 1102
- equals.event_id: 4616
- equals.event_id: 4624
- equals.event_id: 4625
- equals.event_id: 4634
- equals.event_id: 4647
- equals.event_id: 4648
- equals.event_id: 4657
- equals.event_id: 4672
- equals.event_id: 4688
- equals.event_id: 4689
- equals.event_id: 4720
- equals.event_id: 4722
- equals.event_id: 4725
- equals.event_id: 4726
- equals.event_id: 4728
- equals.event_id: 4732
- equals.event_id: 4733
- equals.event_id: 4756
- equals.event_id: 4776
- equals.event_id: 4778
- equals.event_id: 4779
- equals.event_id: 4880
- equals.event_id: 4881
- equals.event_id: 4886
- equals.event_id: 4887
- equals.event_id: 4896
- equals.event_id: 4898
- equals.event_id: 5140
- equals.event_id: 5142
- equals.event_id: 5144
- equals.event_id: 5632
- equals.event_id: 6272
- equals.event_id: 6280
- name: System
processors:
- drop_event.when.not.or:
- equals.event_id: 12
- equals.event_id: 13
- equals.event_id: 104
- equals.event_id: 1074
- equals.event_id: 1116
- equals.event_id: 1119
- equals.event_id: 4697
- equals.event_id: 7000
- equals.event_id: 7045
- equals.event_id: 20250
- equals.event_id: 20274
- equals.event_id: 20275
output.logstash:
hosts:
- 192.168.0.1:5044
logging.to_files: true
logging.files:
path: C:/ProgramData/winlogbeat/Logs
logging.level: info
best,
Lyubo